Introduction
The modern workplace has undergone a seismic shift, with remote work becoming the new norm. This transition, while offering flexibility, presents significant security challenges. Traditionally, companies faced the daunting task of publicly exposing internal services, coupled with the complexities of in-house authentication systems, to enable remote access. While custom VPNs provided a more secure alternative, they often came with a heavy maintenance burden and a significant margin for error.
The Solution
Enter Tailscale, a mesh network VPN tool built on the existing foundation of WireGuard. Tailscale simplifies the creation of secure, private networks, allowing for easy access to internal resources without the complexities of traditional VPNs. Moreover, its powerful Access Control Lists (ACLs) enable specific control over network traffic, ensuring adherence to existing company security policies.
User Authentication
To integrate within your company, Tailscale delegates user authentication to your own existing identity provider (IdP) or single sign-on (SSO) provider such as:
- Apple
- Google and Google Workspace (G Suite)
- GitHub
- Microsoft and Microsoft Entra ID
- Okta
- OneLogin
It also allows custom OpenID Connect (OIDC) providers.
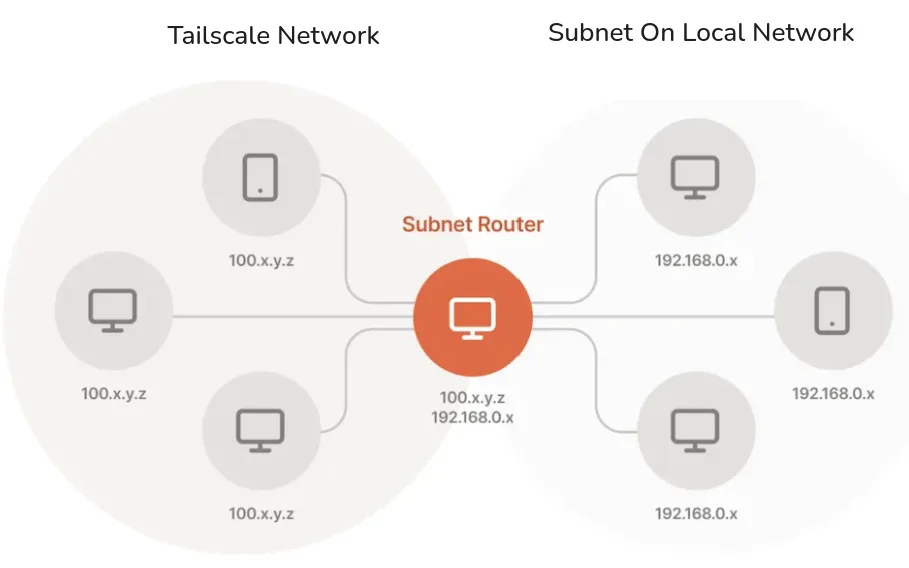
Subnet Routing
Subnet Routing is a massively helpful feature that advertises the local subnet of a specific device to anyone else on the Tailscale network (can change access control in the ACL).
For example there is a company router that is on the same local network (192.168.0.x) as peripheral devices that can not be connected to the Tailscale network (can not install Tailscale software on them), such as old printers or IoT devices. To fix this issues we just have to enable the Subnet Routing option and pick which subnet should be advertised and that is it. Now anyone on the Tailscale network can securely access those peripheral devices !
Tailscale Setup
Download the appropriate OS version from the Tailscale site, https://tailscale.com/download/linux
Then authenticate with your IdP or SSO solution.
Do the same for all other devices (would be wise to only add a few devices now and the rest when we have our ACL rules in place)
Login to your admin console on the Tailscale website and head over to the “machines” tab.
Here is an example of what it looks like with 4 devices connected (ignore the tags and boxes for now):
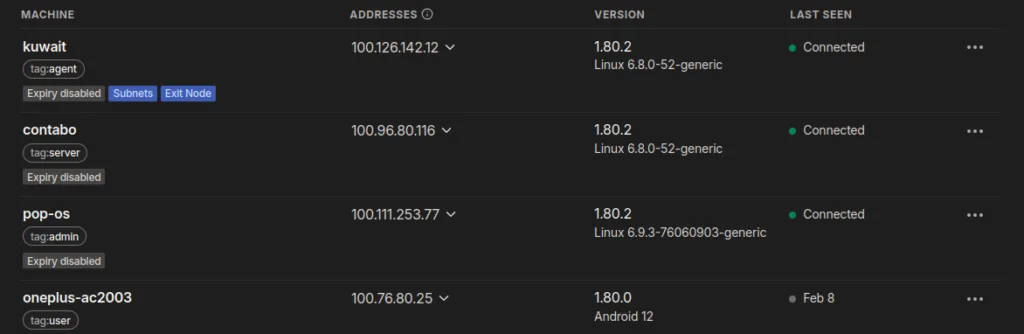
Initially all traffic is allowed so now would be a good time to test the connectivity between devices using the Tailscale local IP addresses (these will only change from direct user action). In my case they start with 100.x.x.x
Edit ACL Rules:
Head on over to the “Access Control” tab. We should comment out the rule that allows all connections.
Now we need to establish tags that we will give to specific devices.
"tagOwners": {
"tag:admin": ["[email protected]"],
"tag:user": ["[email protected]"],
},The user [email protected] owns these tags and he can assign them to devices on the Tailscale network.
Now lets add rules to the acls array
"acls": [
{
"action": "accept",
"src": ["tag:admin"],
"dst": ["*:*"],
},
{
"action": "accept",
"src": ["tag:user"],
"dst": ["100.126.142.12:*"],
},
],In the above code, the first rule allows traffic from source devices with tag admin to any destination and via any port. The second rule allows traffic from devices with the user tag to a specific Tailscale local network IP 100.126.142.12 via any port.
All other traffic that does not match these rules is denied.
There is still much more that we can do and all information can be found on the official Tailscale documentation. https://tailscale.com/kb
Conclusion
We learned to use a modern, secure, and manageable solution to the challenges of remote access. By using Tailscale which, integrates seamlessly with existing identity providers, and offers granular control through ACLs and subnet routing, it empowers organizations to embrace the flexibility of remote work without compromising security. This setup, as demonstrated, allows for precise control over network traffic, ensuring that only authorized users and devices can access specified resources. While this overview provides a solid foundation, the full potential of Tailscale can be explored further in its comprehensive documentation. By implementing these principles, companies can significantly strengthen their security posture in today’s increasingly distributed work environment.